Gulf states using Israeli spyware to target activists and religious minorities
Gulf states using Israeli spyware to target activists and religious minorities
Israeli-made spyware is being used by Gulf states to crack down on dissidents, a new report by Citizen Lab has revealed.
3 min read
Israeli spyware has been used to target dissidents across the region [Getty]
Gulf states are using Israeli-made spyware to target activists and religious minorities at home and abroad, a new report from Citizen Lab has revealed.
The software, named Pegasus, is believed to have been purchased by a number of Arab countries - including Saudi Arabia and the UAE - on the pretext of counter-terrorism and law enforcement.
But Citizen Lab's report indicates that a number of Gulf states - likely the UAE, Saudi Arabia and Bahrain - are using Pegasus spyware to snoop on activists.
It reveals that the UAE has the highest intensity of "infections" from the Israeli-made spyware, suggesting that suspected dissidents have been widely targeted.
The report tracks users of the software - produced by Israeli tech firm NSO and sold to governments around the world to aid in counter-terrorism and law enforcement - and points to residents in the UAE, Saudi Arabia and Bahrain being under the watch of government security agencies - and likely because of their political views.
In order for an individual to be tracked, the government operator must trick them into clicking a link to a website on their movile phone.
Members of the Shia minority and critics of the Saudi-led war in Yemen are among the targets due to the political and religious themes of proxy websites set up by surveillance agencies.
One such operator discovered by Citizen Lab, named PEARL, established a number of fake politically-motivated sites, including shia-voice.com, in an effort to ensnare dissidents from Bahrain's disenfranchised Shia majority.
Another, named FALCON, targeted opponents of the Yemen war in the UAE with the site nomorewarnow.com.
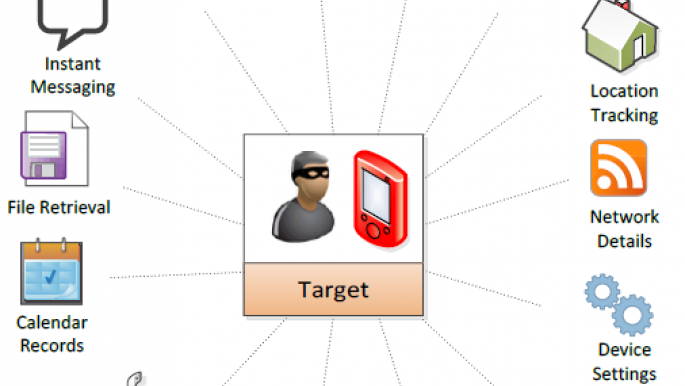
Once links were clicked - either sent as messages or through the websites - the software was secretly downloaded to their phones and activated, allowing spies to monitor voice calls, emails, calendar events and passwords.
Agents could even use the software to switch on phone cameras and microphones to record live events, effectively creating a huge multinational web of spy cameras, broadcasting back to the spyware operator's location without the person being targeted having any knowledge of being spied upon.
The site has previously highlighted the case of Emirati activist Ahmed Mansoor, who was targeted with the spyware after clicking on a link sent to his phone promising to reveal "new secrets" about detainees tortured in UAE jails.
Mansoor was sentenced to ten years in jail in 2018 for critical social media posts, after he was detained by UAE authorities in 2017.
"The GCC countries are well known for abusing surveillance tools to track dissidents. In August 2016, UAE activist Ahmed Mansoor was targeted with NSO Group's Pegasus spyware after previously being targeted with spyware from FinFisher and Hacking Team," the report states.
Citizen Lab pointed out that Bahrain is "noteworthy for compromising journalists, lawyers, opposition politicians, and pro-democracy activists" with another spyware programme between 2010 and 2012.
Amnesty International revealed this year that a member of staff and a Saudi activist working with the organisation has been targeted using Pegasus.
"The same operator responsible for that targeting appears to be conducting surveillance across the Middle East, as well as in Europe and North America," the report states.
The software, named Pegasus, is believed to have been purchased by a number of Arab countries - including Saudi Arabia and the UAE - on the pretext of counter-terrorism and law enforcement.
But Citizen Lab's report indicates that a number of Gulf states - likely the UAE, Saudi Arabia and Bahrain - are using Pegasus spyware to snoop on activists.
It reveals that the UAE has the highest intensity of "infections" from the Israeli-made spyware, suggesting that suspected dissidents have been widely targeted.
The report tracks users of the software - produced by Israeli tech firm NSO and sold to governments around the world to aid in counter-terrorism and law enforcement - and points to residents in the UAE, Saudi Arabia and Bahrain being under the watch of government security agencies - and likely because of their political views.
In order for an individual to be tracked, the government operator must trick them into clicking a link to a website on their movile phone.
 |
| [click to enlarge-Citizen Lab] |
Members of the Shia minority and critics of the Saudi-led war in Yemen are among the targets due to the political and religious themes of proxy websites set up by surveillance agencies.
One such operator discovered by Citizen Lab, named PEARL, established a number of fake politically-motivated sites, including shia-voice.com, in an effort to ensnare dissidents from Bahrain's disenfranchised Shia majority.
Another, named FALCON, targeted opponents of the Yemen war in the UAE with the site nomorewarnow.com.
Once links were clicked - either sent as messages or through the websites - the software was secretly downloaded to their phones and activated, allowing spies to monitor voice calls, emails, calendar events and passwords.
Agents could even use the software to switch on phone cameras and microphones to record live events, effectively creating a huge multinational web of spy cameras, broadcasting back to the spyware operator's location without the person being targeted having any knowledge of being spied upon.
The site has previously highlighted the case of Emirati activist Ahmed Mansoor, who was targeted with the spyware after clicking on a link sent to his phone promising to reveal "new secrets" about detainees tortured in UAE jails.
Mansoor was sentenced to ten years in jail in 2018 for critical social media posts, after he was detained by UAE authorities in 2017.
"The GCC countries are well known for abusing surveillance tools to track dissidents. In August 2016, UAE activist Ahmed Mansoor was targeted with NSO Group's Pegasus spyware after previously being targeted with spyware from FinFisher and Hacking Team," the report states.
 |
| [Citizen Lab] |
Citizen Lab pointed out that Bahrain is "noteworthy for compromising journalists, lawyers, opposition politicians, and pro-democracy activists" with another spyware programme between 2010 and 2012.
Amnesty International revealed this year that a member of staff and a Saudi activist working with the organisation has been targeted using Pegasus.
"The same operator responsible for that targeting appears to be conducting surveillance across the Middle East, as well as in Europe and North America," the report states.
The spyware is being used by government agencies in 46 countries, the report found, including Algeria, Bahrain, Bangladesh, Brazil, Canada, Cote d'Ivoire, Egypt, France, Greece, India, Iraq, Israel, Jordan, Kazakhstan, Kenya, Kuwait, Kyrgyzstan, Latvia, Lebanon, Libya, Mexico, Morocco, the Netherlands, Oman, Pakistan, Palestine, Poland, Qatar, Rwanda, Saudi Arabia, Singapore, South Africa, Switzerland, Tajikistan, Thailand, Togo, Tunisia, Turkey, the UAE, Uganda, the United Kingdom, the United States, Uzbekistan, Yemen and Zambia.



